What is a firewall and how does it work?
Hacking attacks are often pretty minor and can include things such as personal data theft for the purpose of extortion. These attacks usually fail, but can sometimes be really devastating when the subject is a business or government organisation; we’re talking huge monetary losses. There are a huge variety of applications and software that were created to protect users from theft of data that is kept on their electronic devices or online accounts, and one of them is a firewall.
What is it?
A firewall is a network security system that filters incoming and outgoing network traffic according to the firewall's rules settled by a user. The main goal of the firewall is to minimise or just to remove undesired network contacts and let in all admissible communication. Firewalls are a significant part of cybersecurity and can be used in parallel with other tools to provide a high level of personal data security.
Firewalls are useful for every Internet user, no matter if we’re talking about a company or an individual user. Hackers can attempt to exploit every computer connected to the network in their malicious purchases. Your computer might be hacked in order to spread damaging links through your email or social networks accounts. That’s why you should be aware of how to protect yourself from breaches.
A firewall can be built into an operating system; an ordinary user usually doesn’t notice the work of this protective system until it reveals a threat in an incoming file.
What is inside it?
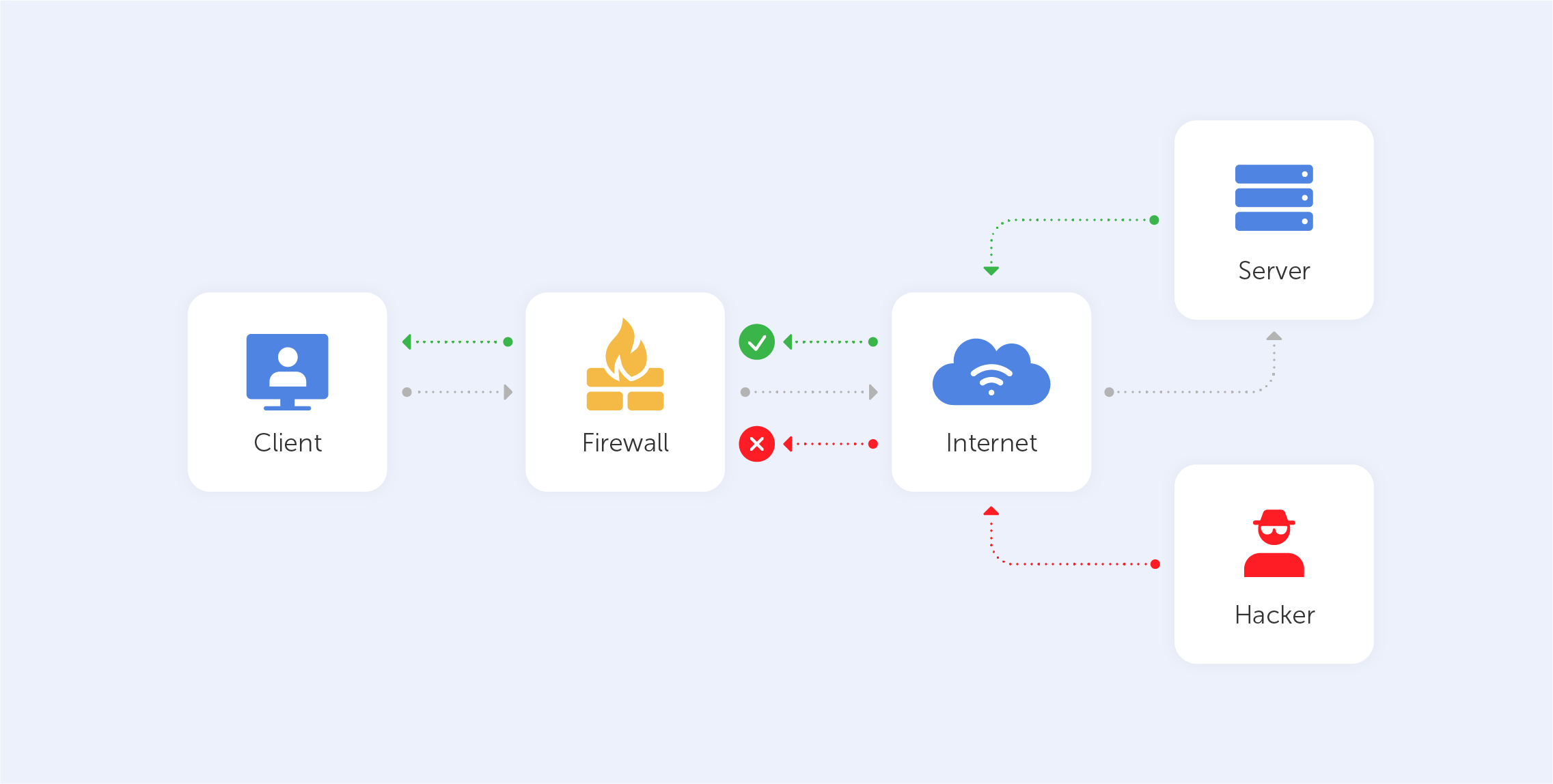
A firewall could be a type of software or hardware that looks for threatening elements that have been flagged as dangerous. Hardware options for intercepting traffic travelling between the broadband router and user devices are frequently included in routers. Software options are programs that track the data that enters and exits your computer. Regardless of the type, the main function of the firewall is to block the access or dispatching of data packets that have been identified as a safety risk. This reversible security system not only protects your computer from attacks but also prevents the spread of malicious data through the network. It can also be used to block unwanted applications.
For example, if an employer wants to control the work of its employees, they’re able to set the system to block certain apps such as Skype, gaming apps, or social networks. Also, firewalls provide an opportunity to block unwanted advertising while controlling access to traffic. A good example of this function can be found when connecting to certain kinds of public WiFi, specifically when you should enter your phone number or email address to get access.
Now let's take a look at the three most common types of firewalls: packet filtering, proxy service, stateful inspection and NGFW. Of course, they are quite different in how they monitor and filter network communication.
Packet filtering
Packet filtering, also known as a ‘stateless’ firewall, analyses particular packets (little data units) one at a time using a set of filters. Thus, the system finds out and stops packets that contain danger while allowing the rest to proceed to their destination. This type of firewall is based on the filtration of unique headers of the packets — the main part that contains basic data like the origin of the packet and its destination.
Proxy service
An application firewall (or proxy service) is quite an efficient tool. It acts as a cyber agent rather than a filtering system. They safeguard your network location from any malicious actors by effectively producing a ‘mirror’ of the computer behind the firewall that excludes the possibility of direct communication between your computer and the information itself. But this type has some flaws. Primarily, it works slower than firewalls of other types and generally has application limitations.
Stateful inspection
Stateful firewalls are more versatile than the previous types as they are able to evaluate not only the headers of the packets but also the variety of aspects that each data lot contains. To pass the firewall, the incoming packet must correspond to the trusted information defined by the firewall rules. This type of firewall is the most streamlined and provides efficient security.
NGFW
The last genus of firewalls is also attributed to application firewalls, although developers usually call them next-generation firewalls (NGFW). This type includes the best of the previous generations of firewalls and also includes a more comprehensive double-checking of packets. It prevents system mistakes in detecting potentially threatening traffic. The newest firewalls are also equipped with extra security systems like VPNs, IPSs (intrusion prevention systems), and identification control systems. This allows users to utilise just one app or kind of software for multi-layer security.
By using firewalls, you mitigate the risks of data theft and the unauthorised entry into your personal devices and accounts. These systems provide safety by establishing protective filters inside every part of your network to detect and eliminate threats like backdoors, viruses, remote logins, or spam.
Also, firewalls vary depending on their appointment. Some of them were created for personal or small-group (under 100 people) use. A good example is a firewall that is built into the Windows operating system. Others have been developed for companies with 1,000 or more employees. These ones should be attentively set up and are usually controlled by an in-house company programmer.
Now, let's talk a bit more about system-based firewalls. As previously stated, traffic that passes through a firewall is compared with the firewall's rules to figure out whether it can be accepted into the system or not. The program contains a list of rules which is consistently compared with incoming data packets. Every rule begins with an index word: accept, drop or reject. The system acts according to those words and the following directions. If the packet satisfies the direction indexed with ‘accept’, it’ll be accepted. Indeed, if it satisfies the ‘reject’ direction, that traffic will be blocked with an ‘unreachable’ error tag. Also, the ‘drop’ means that the traffic will be blocked without sending a reply.
That is, of course, just a ‘tap on the water’ explanation of what a firewall is. For a deep dive, visit https://www.bu.edu/tech/about/security-resources/host-based/intro/.

