The brute force attack: definition and examples
What is a brute force attack?
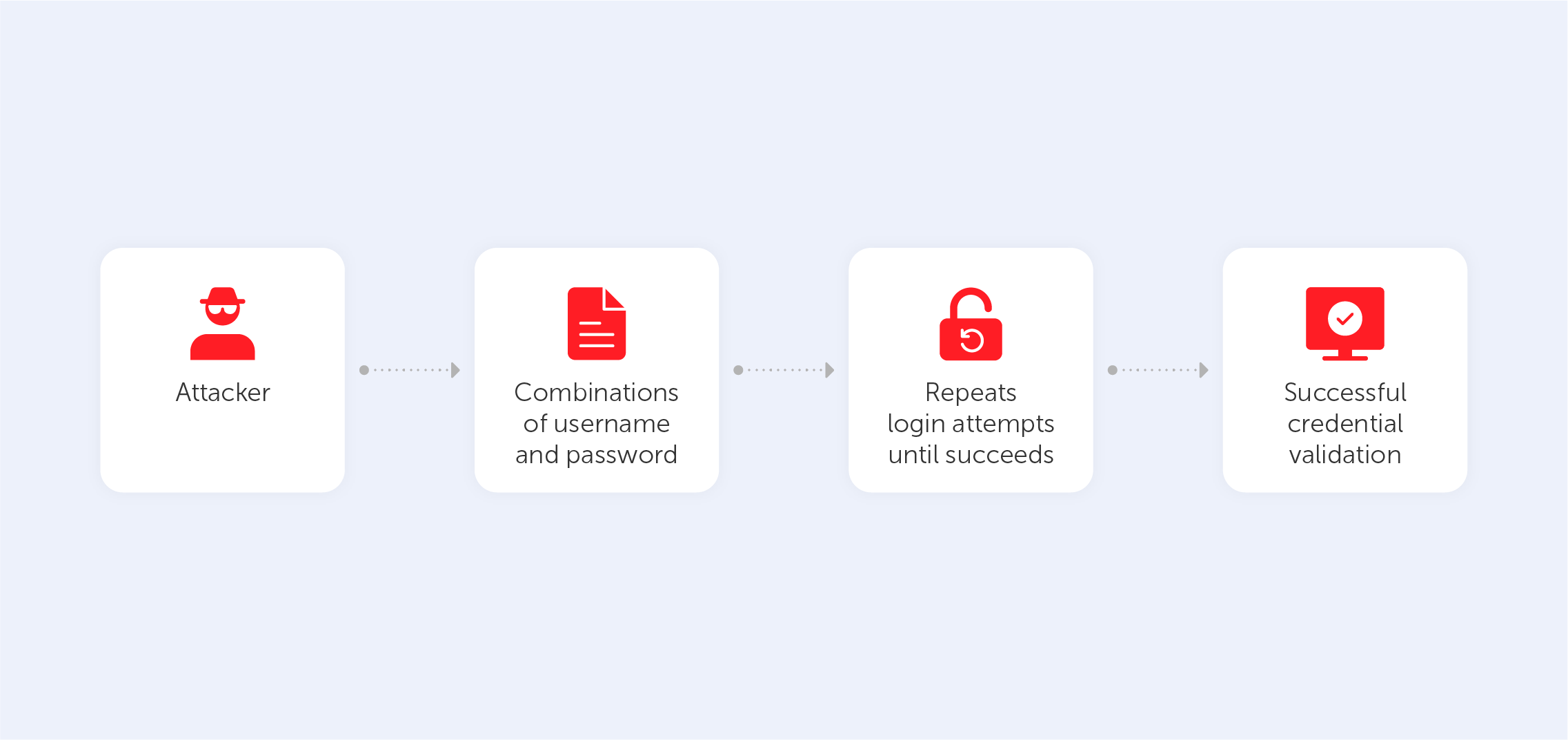
Among a myriad of different cyberattacks, the brute force attack seems to be the most common and primitive way of hacking. This technique involves guessing login information through trial-and-error, where hackers try all conceivable combinations in the hope of guessing correctly.
The term “brute force" refers to the method itself, being both brutal and forceful. Despite the fact that brute force attacks are a pretty ancient cyberattack approach, they still remain a prominent technique among modern-day hackers.
Types of brute force attacks
A brute force attack can be split into a few different types, each kind employing a variety of techniques that serve to unearth your private data. You should be aware of how cybercriminals apply each type in order to ensure maximum protection.
1. The simple brute force attack — this refers to the process of simply guessing the login credentials via logical deliberation, without the use of any software. Hackers just go through every standard combination of letters and numerals, perhaps combining this with some information that they know about you. This method is cumbersome yet reliable as many people still use primitive and common passwords and PINs like “user1” or “12345” in order to remember it easily. Also, users, who use the same password for every account put themselves in extra danger; if the hacker does guess one password correctly, then it’s likely that they’ll be using that password as the first port of call when it comes to other accounts.
2. A dictionary attack — this is a type of brute force attack that involves the user submitting a very large variety of different password combinations. Although this kind of assault is technically a brute force attack, it takes a significant place in the process of cracking passwords. The name of this technique comes from the actions that a hacker performs during the break-in attempt. The criminals scan through password dictionaries modifying words using different numbers and abbreviations. It usually takes a lot of time and has poor success rates when compared to newer techniques. However, it’s easy to do if you have a computer at your disposal.
3. A hybrid brute force attack — this type combines the two that we’ve just looked at: the brute force attack and the dictionary attack. Combination passwords, which mix common words with random characters, are cracked using these approaches. Usually, it starts with a certain username which is used as a base for the following actions: hackers input a list of words that potentially could be included in the password, then combine them with different characters and numbers until they reach the correct password.
4. Reverse brute force attack — contrasting with other types of brute force attack, the reverse attack starts with a known password. Usually, hackers get these from leaked databases that are freely available on the internet. Attackers choose one password and look through millions of accounts until one matches. Of course, it’s easier for the criminal to locate a match when the password includes a name or a birth date, so it’s better to avoid using such information in your password.
5. Credential staffing — this type of attack is based on users’ cybersecurity illiteracy. Hackers collect and store lists of already cracked or stolen passwords and usernames connected to them and then go through dozens of other websites to see if they can obtain access to other accounts of the same user. Thus if the person utilises the same password for various social networks, apps and websites, he or she allows the attacker to get every bit of private information contained on each account.
6. Botnets — this type of attack can be combined with any of the above. The main point of a botnet attack is to use extra computational resources to attack the victim. This way, hackers manage to avoid the costs and difficulties associated with running programs on their own systems by exploiting hijacked machines to carry out the brute force attack. Furthermore, the usage of botnets provides an additional layer of anonymity which is also desirable for hackers.
Brute force attack tools
It can take a long time to crack the password of somebody’s email or website, so hackers have created some software to assist them in breaching accounts, which makes the process easier and faster.
1. Aircack-ng is a toolset that provides the hacker with the opportunity to enter various Wi-Fi security systems. They’ll be able to monitor and export data through the use of this software. They can even hack companies using techniques such as spoofing access points and packet injection. Such software is free and can be acquired by anyone.
2. DaveGrohl is a brute-forcing tool that was made to assist in dictionary attacks. It offers a mode that helps hackers to attack a victim using the force of several computers.
3. John the Ripper is a program made for recovering passwords. It supports thousands of encryption systems including those used in macOS, Unix, Windows, various web applications, network traffic, and document files.
These programs can quickly go through all conceivable combinations and choose the correct one to breach a variety of computer protocols, encrypted information storage systems and modems.
Examples of brute force attacks:
Brute force attacks are so common that almost every person or organisation has at least once fallen victim. Even worldwide organisations that are known for their robust security systems could be exposed to a brute force attack. For example, in 2018, it was uncovered that Firefox’s master password was quite easy to figure out. Because of this, nobody knows how much personal data was actually leaked into the network. This wasn’t the only brute force attack to occur that year. Unknown hackers compromised the accounts of numerous members of the Parliament of Northern Ireland.
Three years before that, Dunkin Donuts, a doughnut and coffee franchise, became a victim of another brute force attack that resulted in people losing large quantities of money due to a breach that took place in the company’s mobile app. Cybercriminals utilised brute force to obtain illegal access to the credentials of more than 19 thousand people, eventually taking their money. Unfortunately, the company didn’t make users aware of the attack and people couldn’t take the appropriate precautions to protect their personal data and money in the future, so a complaint was eventually filed against it.
Despite most people actually being aware of the measures required for privacy maintenance, a lot of users still disregard the rules of cybersecurity by trying to simplify access to their accounts with a simple, reusable and easily memorable combination. This way, they make themselves potential victims of brute force attacks, which are largely possible thanks to the carelessness of cyber-civilians.

