The popularity of push notifications can be easily explained – marketers have noticed that customers are more likely to read short messages that don't need to be opened and are more likely to click on links contained within them. Therefore, various companies have long adopted and actively used this communication channel with customers. However, malicious actors use push notifications for phishing, spreading malware, and other cyber threats. This article discusses the schemes used by malicious actors, what service developers need to consider, and how not to become a victim of fraudsters.
How malicious actors use push notifications
A push notification resembles an SMS, consisting of a title and a short message, an icon with the sender's name, and it may also include an image and buttons to perform a certain action, such as clicking a link. Additionally, the differences between push notifications and SMS include that the latter are received on any model of mobile phone and are delivered through mobile operators. Receiving push notifications requires a smartphone that supports this feature, the installation of applications, and internet access. Users can manage notifications themselves: prohibit, fully allow, or partially allow. Push notifications are usually stored in the personal account on the website, in the application, or in the notification center if the phone is on iOS and in the notification log if you have Android 10 and above.
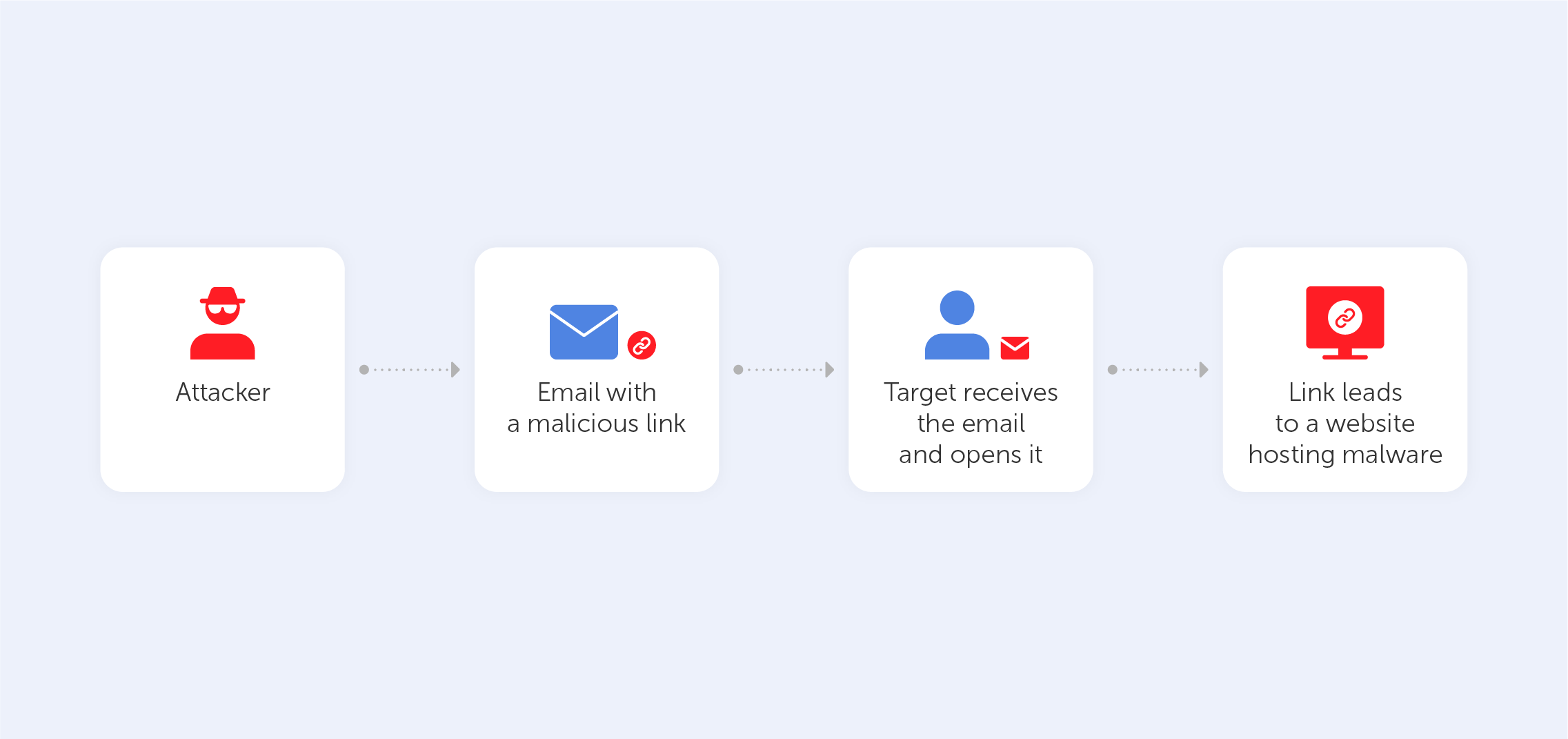
The most common methods include sending push notifications that masquerade as official notifications from banks, online stores, or other services to prompt users to enter personal data or bank card details on phishing sites. One of the freshest instances involved a victim showing their screen to fraudsters, who posed as a bank security service and saw all push notifications with confirmation codes, allowing them to rob the victim.
From the users' perspective, push notifications seem convenient. A person receives dozens of pushes a day – from media, banks, marketplaces, and messengers. The short texts inform about discounts, new stock arrivals, promotions, and reminders. Moreover, push notifications deliver alerts about funds being debited or credited, codes for authentication, and access to one's account or personal cabinet on various services and sites. Malicious actors exploit this – due to the large amount of incoming information and often, lack of attention, a victim of fraud can easily click on a link in a pop-up "push."
Among relatively new attack methods is the ‘Fatigue’ attack, another form of social engineering. The essence of this method is to send the user a large number of login confirmation requests, thereby catching him off guard and scattering his attention. Eventually, the person is likely to accept the request to eliminate the "spam" on their phone or decide that the system is broken and that they need to "press the button" to fix everything.
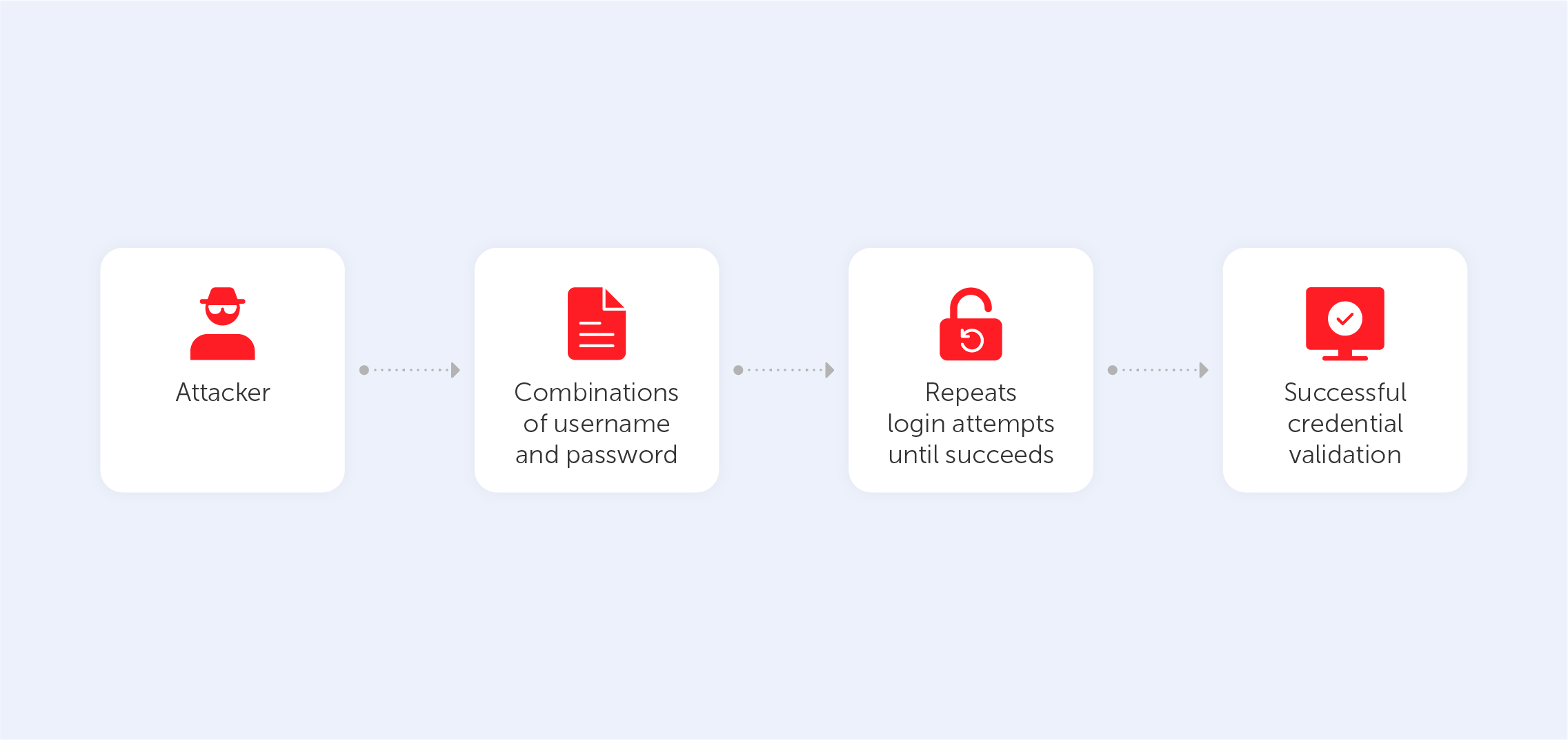
The attack targets users whose first factor, most often a password, has already been compromised, although this is not such a big problem, considering the size of leaked password databases. By overcoming the two-factor authentication system in this way, malicious actors penetrated some corporate systems of Uber, Microsoft, and Cisco, and in 2024, Apple users faced this issue. Since successful attacks on large corporations continue, it can be concluded that businesses are not yet ready to repel such attacks.
In late February 2024, The Washington Post published an article about a new method the FBI uses to surveil suspects using push notifications. The agency filed more than 130 orders to disclose data of push notifications in 14 states. This became possible thanks to a feature of "pushes." When a user registers in an app, Apple and Google servers create and store a unique identifier - the "push token." This token can later be used to identify a person using the app based on device information.
Data protection advocates are concerned that this capability poses a threat to users' privacy from both the state and malicious actors. To send a victim push notifications, a fraudster must infect the device with malware. For example, the banking trojan Ginp was discovered by Kaspersky Lab. In addition to the standard set of abilities for a banking trojan: transmitting the entire contact list to its owners, intercepting SMS, and overlaying the screen with fake pages, the malware uses fake push notifications to convince the victim to open a phishing page.
Recommendations for service developers
Before connecting push notifications to a service, it's recommended to study their weaknesses and plan for data protection from leaks. Limit the information transmitted to the push notification service, including metadata.
There are several security measures. Firstly, do not use Push notifications to access valuable digital resources. Instead, use other protection tools for login, such as TOTP or physical tokens with a built-in password generator or digital certificate.
Secondly, implement throttling mechanisms in server systems for sending Push notifications. A well-designed push factor should offer the user options to reduce automatic responses. For example, it displays several options with numbers, and the user must choose what they see on the device they are logging in from.
Thirdly, report attack attempts to SOC and make quick decisions on temporarily blocking compromised accounts. Also, the importance of encryption when working with push notifications cannot be overlooked. And remind users of cybersecurity rules to prevent illegitimate actions by malicious actors.
For user protection, developers should follow several principles:
Сontent validation
Before sending a notification, ensure it doesn't contain potentially dangerous links or requests;
Use of secure protocols
All communication between the app and server, as well as the push notification server, should use encryption (e.g., via HTTPS);
Regular updates and dependency control
Used libraries and dependencies should be regularly updated to avoid known vulnerabilities;
User education
Provide information about notification settings and the dangers of fraudulent messages.
Protection measures
To avoid becoming a victim of fraudsters, users need to follow several rules, including being vigilant not automatically accepting offers, and not thoughtlessly clicking on links from ‘Pushes’. For security when using push notifications, users should only download official bank apps from their official websites and avoid installing apps from unverified sources.
Be cautious with push notifications about transactions and password change requests – verify such information through official communication channels with the bank.
Push notifications can appear on device lock screens, allowing unauthorized access to information in push notifications if the device falls into the wrong hands. Add a screen lock and configure the allowable information to be displayed on the screen for push notifications.
It's better to simply disable unnecessary notifications, and delete unnecessary apps from the phone. When "pushes" can be sent by a limited number of services, it's easier to notice a suspicious message.
Wrapping up
In summarizing our exploration into the realm of push notifications, it's evident that these alerts occupy a significant role in our digital ecosystem. They serve as efficient conduits for information, offering immediate updates on transactions, sales, and various notifications directly relevant to our daily activities. However, this convenience also presents an avenue for malicious entities to exploit, using these notifications as a means to deploy phishing attacks, distribute malware, or engage in identity theft.
Despite these vulnerabilities, there is a concerted effort from the development community to enhance the security and integrity of push notification systems. Through the adoption of encryption and the implementation of more rigorous security protocols, developers are creating a more resilient framework to protect users from potential threats. Additionally, there is an emphasis on user education, encouraging individuals to exercise discretion and vigilance when interacting with push notifications.
For users, adopting a proactive approach to digital hygiene can significantly mitigate the risks associated with push notifications. This includes verifying the authenticity of apps before downloading, being cautious about the personal information shared within apps, and utilizing the security features provided by their devices. Periodically reviewing and customizing notification settings can also prevent unauthorized access to sensitive information, further safeguarding against fraudulent activities.
Ultimately, push notifications represent a dual-faceted feature of modern technology – providing essential information swiftly while posing potential security risks. By fostering a culture of awareness and implementing robust security measures, both developers and users can navigate these challenges effectively. As we continue to integrate these notifications into our daily lives, maintaining a balance between convenience and security will be paramount. In doing so, users can leverage the benefits of push notifications without compromising their digital safety.