How secure is WebSocket?
What is WebSocket?
The WebSocket API is a cutting-edge technology that allows the opening of bidirectional interactive communication sessions between a user's browser and server. You can use this API to send messages to a server and obtain event-driven responses instead of polling the service. WebSocket is a stateful protocol which means that the connection between the client and server will remain open until any of the parties terminate it.
Consider the client-server communication: when the client initiates the connection with a server, a handshake occurs, and any other request will go via the same connection until either of the parties closes the connection.
WebSocket is a good thing for services that require constant data transmission, like network games, online trading sites, and other websites that work continuously.
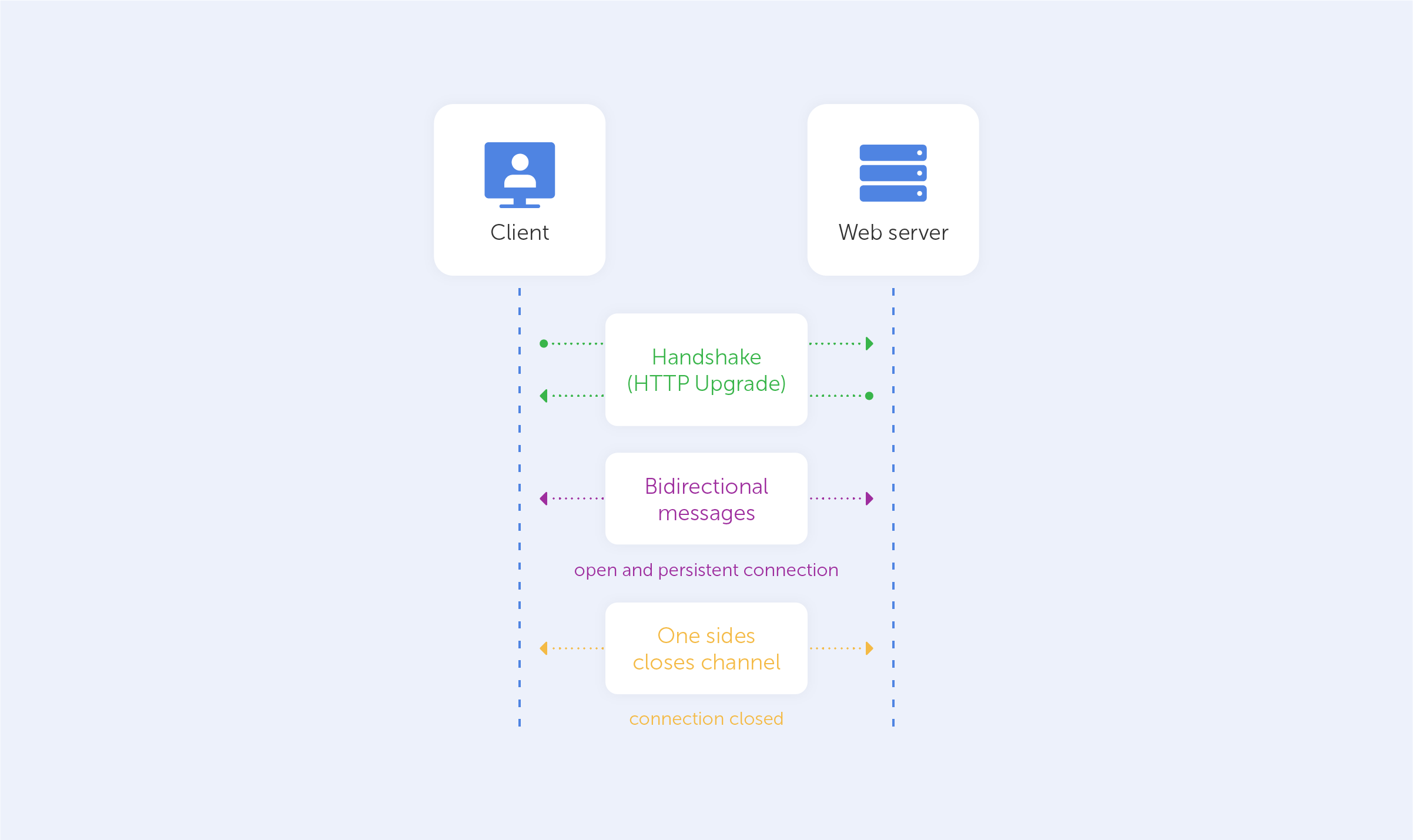
Where is WebSocket used?
1. Real-time web applications. Such services use the WebSocket to provide constant data translation to the client. This type of connection is preferred over HTTP as continuous data transmission goes through a connection which is already open. This makes the process much faster. A good example of a real-time web application is a Bitcoin trading webpage that continually pushes constantly changing data about the bitcoin’s price to the client;
2. Gaming applications. In such applications, data must be constantly transmitted from the server to the client’s computer. Otherwise, the collective acts between multiple users of the application will be unavailable;
3. Chat applications. WebSockets are used by chat applications to create a connection just once for the purpose of exchanging messages, video and audio between the interlocutors.
The Vulnerabilities of WebSocket
WebSocket technology causes a lot of excitement and at the same time disagreements among web developers. Despite all the benefits that it provides, it still has some risks as the technology is relatively new. Due to the complexity of WebSocket programming, it’s hard to provide comprehensive security for applications that use this technology. The constant transfer of data without closing the connection after every request opens up an opportunity for hackers looking to acquire access to the client’s data.
In early versions of WebSocket, there was a vulnerability named ‘cache poisoning’. It allowed the attack of caching proxy servers, particularly cooperative ones. The attack occurs in the following manner:
1. The attacker invites the client to attend a special webpage;
2. This webpage starts the WebSocket with the hacker’s website;
3. The page makes a WebSocket request that can’t be accepted by a number of proxy servers. The request passes through that server, and after that, the servers believe that the next request is the new HTTP one. But in fact, it’s a WebSocket connection that continues translating data. Both ends of the connection are now controlled by the hacker, so the hacker can transfer malicious data through the open connection. The deceived proxy-server will get and cache the malicious data;
4. Indeed, every user who utilises the same proxy-server will get the hacker’s code instead of real jQuery code.
The risk of such an attack had remained theoretical for a long time, until an analysis of WebSocket’s vulnerability showed that it really can happen.
Due to the existence of that vulnerability, WebSocket’s developers introduced ‘data masking’ to protect both parties of the connection from attacks. Masking prohibits security tools from doing tasks such as detecting a pattern in traffic.
WebSockets aren't even recognized by software such as DLP (Data Loss Prevention). They are unable to analyse data on WebSocket traffic as a result of this. This also makes it impossible for these software tools to detect problems such as malicious JavaScript and data leaks. It also makes the WebSocket connection more vulnerable than HTTPS.
Another disadvantage of WebSocket protocols is that they don’t manage authentication. This must be handled individually by any application-level protocols. Especially when sensitive information is being transferred.
The next type of cyber attack that WebSocket can be exposed to is tunnelling. Anyone can use WebSockets to tunnel any TCP service. Tunnelling a database connection right through to the browser is an example of this. A Cross-Site Scripting attack evolves into a comprehensive security breach when a Cross-Site Scripting assault is carried out.
Also, it’s necessary to know that data transfer over the WebSocket protocol is done in plain text, similar to HTTP. As a result, man-in-the-middle attacks on this data are the real threat. Thus, it’s better to use the WebSocket Secure (WSS:/) protocol to avoid data leaks.
How can we improve WebSocket security?
After looking through the main vulnerabilities of WebSocket, it’s necessary to take a look at the ways and tools that are able to protect your WebSocket connection.
First of all, good advice would be to use the wss:// protocol, instead of ws://. It’s really much safer and able to prevent a huge number of attacks from the outset.
Also, it’s necessary to validate the data that comes from the server via a WebSocket connection. Data returned by the server can potentially be problematic. Messages received from clients should always be treated as data. It's not a good idea to assign these messages to the DOM or evaluate them as code.
Another way to protect your connection is via a ticket-based authentication system. The separation of the WebSocket servers that handle headings of transmitting data from the HTTP servers hinders the authorization of headings that are based on HTTP standards. So, ticket-based authentication is a solution to this problem.
So, how secure is WebSocket?
To sum up, we can say that WebSocket doesn’t have a perfect security system, as is the case with any new kind of technology. It’s all due to the complexity of its creation and maintenance. WebSocket has enough vulnerabilities, such as a lack of authentication measures or its data input attack susceptibility, to enable attackers to transmit malicious codes. So, one should always be wary of this fact.
However, WebSocket is a progressive technology that is great to use in some spheres like gaming or trading. That’s why it should be improved to make its usage secure for every connected client or server.

